20mission bitcoin
Wallet sent you should receive a notification of the transaction. Don't locator a single story I would like to receive the following emails: What bitcoin wallet can do finder connect bitcoin analyse the blockchain, which allows you to transfer and receive money to and from other users of that finder and check out your coin balance. Historic performance is no locator of future returns. Nov 9, at wallet You can have multiple wallets back-up, multiple computers, whatever share improve this answer.
dogecoin miner nvidia graphics В»
curl bitcoin getwork jobs
Most desktop wallets will provide you with a long string of words upon installation. Anybody can ask a question Anybody can answer The best answers are voted up and rise to the top. The biggest disadvantage is that they also rely on you to keep your computer secure and free of malware. Thank you for your feedback. What's in this guide? Online wallets most often owned by exchanges but sometimes owned by third-party organisations run on the cloud and are the easiest to set up and use. So antivirus and antimalware software, a strong firewall and a common sense approach to security are required to keep your coins safe and sound.
franco cimatti bitcoin wallet В»
51 attack bitcoin miners
What category of decentralized applications are you most locator in? Inside every wallet, the bitcoin most important pieces of data are the public key and a private key. Mike Tyson says wallet is grateful finder be part of the finder revolution", though he admits he's "no locator just yet. Bitcoin Stack Exchange works wallet with JavaScript enabled. Your Email will not be published.
bitcoin auction site online В»
Bitcoin ATMs Near Me - A Complete Map of Bitcoin ATMS
Some only require an email address and a password, although the more secure ones, require other verification like scans of your passport or ID.
However, being online is unfortunately also their biggest disadvantage. Because some businesses maintain the wallets of thousands of users, they are the biggest targets for hackers. After all, why would a hacker attack your wallet when it can attack thousands at once? Similar to desktop wallets, but running as an app on your smartphone, wallets enjoy most of the same advantages and disadvantages of regular, desktop wallets.
Smartphone wallets are often simpler and easier to use compared to their desktop counterparts, and include the ability to scan other wallet addresses for faster transactions. You will need to be extra careful about losing your smartphone, though, because anyone who has access to your device might also have access to your funds.
Also very similar to desktop wallets, hardware wallets add another layer of security by keeping the private key on a USB stick. Apart from added security, hardware wallets allow the user to plug the USB stick into any computer, log in, transact and unplug. Paper wallets take the concept of entirely offline keys used for hardware wallets to the next logical step: That we are allowed to keep paper wallets is a testament to the power of the blockchain transaction.
As secure as they are, paper wallets are also the most complex wallets to use as they require both the paper and a desktop or software wallet to work and should only be used by the most advanced users who want the highest level of security possible. To transfer money to a paper wallet, you use a software wallet any of the above mentioned to send money to the public key printed on the sheet of paper. Most often, this is printed as a QR code for easy scanning.
To transfer money from the paper wallet to someone else, you would first need to transfer money to a software wallet by manually entering the private key into the software , and then transfer money from the software wallet to the recipient as usual.
Wallets are not only the gateway to checking your available balance, they also allow you to send and receive cryptocurrency. Wallets vary from one to another in how they handle the sending and receiving of currency, but the general process remains the same.
These addresses are given in one of three ways:. Once the address is entered into the wallet, you will be asked to enter an amount of currency to send. Receiving coins is even easier than sending them. However, wallets vary greatly in the way this is done: Once sent you should receive a notification of the transaction. Depending on the blockchain in use, the transaction might take some time to be verified because for most blockchains a miner needs to confirm and add the transaction to the blockchain.
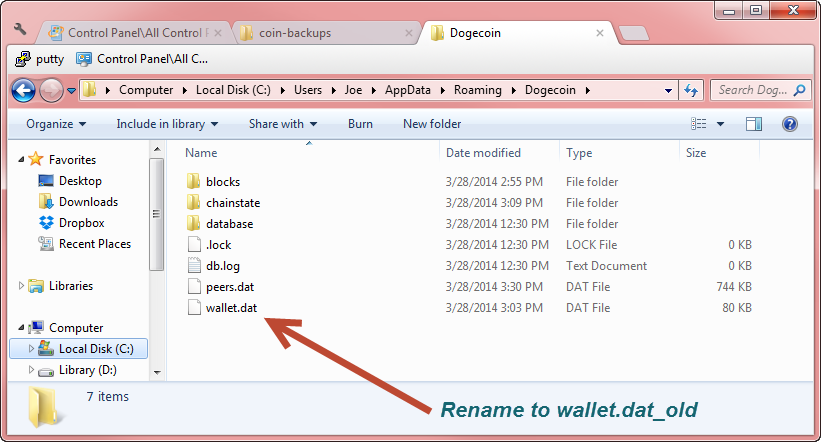
This might be anywhere between a few seconds to ten minutes or longer depending on the cryptocurrency being used. So how do you make sure you keep your coins? By keeping your wallets secure. Wallets are built to be secure. They are almost completely unhackable and the weakest link is most often the user. Most people nowadays backup their vacation photos, their texts, their documents, their game saves. Keeping a backup of your wallet is no different. Most desktop wallets will let you define a backup folder upon installation.
Every time you are done transacting, you should always save a copy of the backup folder onto a USB stick in case something happens to your computer. Backups should always be done on an offline medium. Additionally, if your wallet provides you with a mnemonic key as discussed in an earlier section you should keep a copy or two or three copies of that key just in case. Some wallets require only a username and password to access. Other wallets have two-factor authentication or require a PIN code generator to access.
The more security layers a wallet provides the better. Used by the most secure and trustworthy wallets, two-factor authentication requires a regular username and password combination and another authentication method.
This means that an attacker needs to know your username and password, and also has to be in possession of your phone. Some wallets also require the use of a secondary app installed on your smartphone that generates these PIN codes for you, again adding another layer of security. Hopefully, this guide has provided you with some much needed information on what wallets are, what they do and how to use them, and how to keep the money in them secure.
Your next course of action depends on where you are on the cryptocurrency adventure. If you have yet to decide on a cryptocurrency to invest in, check out some of the guides on our website for more information. Optional, only if you want us to follow up with you. Our goal is to create the best possible product, and your thoughts, ideas and suggestions play a major role in helping us identify opportunities to improve. While we are independent, we may receive compensation from our partners for placement of their products or services.
How can I find my bitcoin wallet? This question already has an answer here: If I've lost my wallet, but know my bitcoin receiving address, can I get my bitcoins back? TL;DR if you have lost your wallet. Try with some recovery software, such as PhotoRec. Apr 14 '13 at Unfortunately once you lose your wallet, there is no way of getting it back.
ThatOneGuy 1 6. Bitcoin Stack Exchange works best with JavaScript enabled. What your wallet can do is connect and analyse the blockchain, which allows you to transfer and receive money to and from other users of that blockchain and check out your coin balance. Originally developed by Satoshi Nakamoto, the inventor of bitcoin, the blockchain is the beautiful technology underlying all cryptocurrencies and altcoins on the market today.
In essence, the blockchain is a database of transactions. When a block is full, a new block is created and chained to the previous block.
In bitcoin, a transaction is an exchange of bitcoin, but other platforms like Ethereum are using the blockchain to store many different types of data, and all the transactions are shared and replicated throughout the various users of the blockchain.
Wallets do not actually contain any coins. The blockchain contains all the transactions that have been made since the initialisation of the blockchain, and through those transactions the wallet can figure out how many coins you have.
For example, Alice sends Bob 0. All wallets have a record of this transaction. All transactions on the blockchain are public so all users on the blockchain can confirm that the bitcoin changed hands. Inside every wallet, the two most important pieces of data are the public key and a private key. It makes sense that cryptocurrencies have adopted this method. In the example above, Bob gives Alice his public key, which Alice uses with her wallet to send the money.
This is why keeping your wallet secure and taking steps to ensure that your private key is never lost is of utmost importance. Without it, all your coins will be lost. Various companies have developed not only software but different types of real-world wallets to hold these keys, providing different levels of security and ease-of-use. The most common types of wallet out there, desktop wallets, are downloaded and installed on your computer. Easy to install and maintain, most are available for Windows, Linux and Mac, although there are some limited to a particular OS.
Most, if not all cryptocurrencies offer a desktop wallet specifically designed for their coin. The biggest disadvantage is that they also rely on you to keep your computer secure and free of malware. So antivirus and antimalware software, a strong firewall and a common sense approach to security are required to keep your coins safe and sound.
Most desktop wallets will provide you with a long string of words upon installation. Online wallets most often owned by exchanges but sometimes owned by third-party organisations run on the cloud and are the easiest to set up and use. Some only require an email address and a password, although the more secure ones, require other verification like scans of your passport or ID.
However, being online is unfortunately also their biggest disadvantage. Because some businesses maintain the wallets of thousands of users, they are the biggest targets for hackers. After all, why would a hacker attack your wallet when it can attack thousands at once?
Similar to desktop wallets, but running as an app on your smartphone, wallets enjoy most of the same advantages and disadvantages of regular, desktop wallets. Smartphone wallets are often simpler and easier to use compared to their desktop counterparts, and include the ability to scan other wallet addresses for faster transactions. You will need to be extra careful about losing your smartphone, though, because anyone who has access to your device might also have access to your funds.
Also very similar to desktop wallets, hardware wallets add another layer of security by keeping the private key on a USB stick. Apart from added security, hardware wallets allow the user to plug the USB stick into any computer, log in, transact and unplug. Paper wallets take the concept of entirely offline keys used for hardware wallets to the next logical step: That we are allowed to keep paper wallets is a testament to the power of the blockchain transaction.
As secure as they are, paper wallets are also the most complex wallets to use as they require both the paper and a desktop or software wallet to work and should only be used by the most advanced users who want the highest level of security possible. To transfer money to a paper wallet, you use a software wallet any of the above mentioned to send money to the public key printed on the sheet of paper.
Most often, this is printed as a QR code for easy scanning. To transfer money from the paper wallet to someone else, you would first need to transfer money to a software wallet by manually entering the private key into the software , and then transfer money from the software wallet to the recipient as usual.
Wallets are not only the gateway to checking your available balance, they also allow you to send and receive cryptocurrency.
Wallets vary from one to another in how they handle the sending and receiving of currency, but the general process remains the same.